Securing AI agents and non-human identities in enterprises
In 2025, NHIs surged with the rise of AI agents, microservices, and distributed cloud systems. This ebook gives you a practical roadmap to secure NHIs in your stack, with Zero Trust principles at the core.
What's inside the ebook
Drawing from hands-on customer work, discussions with security & IAM teams, and
the latest OWASP research, we’ll cover:
-
Incident-driven threat insights
Learn from real-world security breaches at Okta, GitHub, and Microsoft to understand NHI-specific risks.
-
12 principles for NHI governance
Apply 35 actionable steps for adaptive, risk-informed permission and identity management.
-
Vendor landscape & evaluation toolkit
Navigate the ecosystem with a curated vendor map and checklist to guide your implementation strategy.

Created for modern security teams
60 pages
of in depth content
Opinions from
security leaders
Practical
frameworks
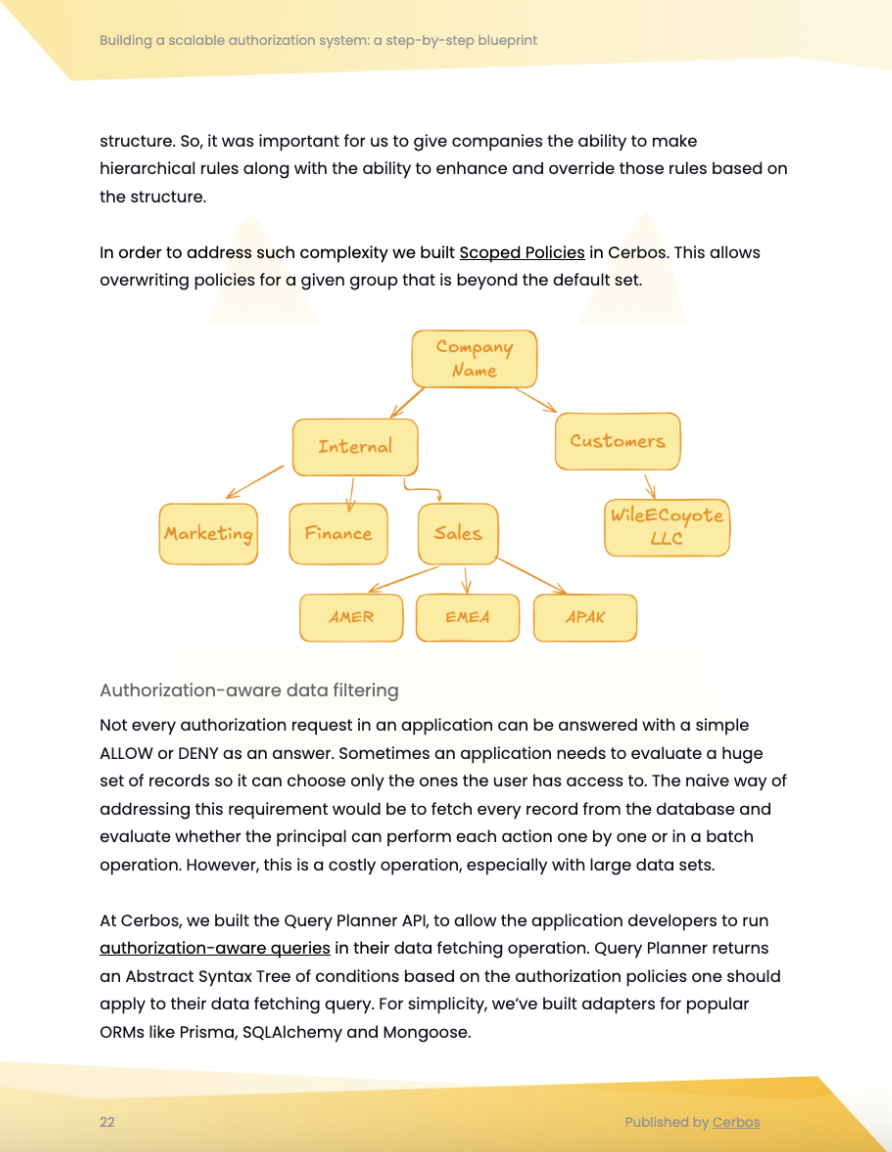
The technical framework you need to secure NHIs across your environments
NHI taxonomy
We’ll lay out a taxonomy of NHIs and explain why NHIs are becoming a major security and compliance concern for our clients and other tech companies. You’ll learn how the explosion of NHIs is creating new vulnerabilities and how agent-based AI is accelerating the risk.
Topics covered: Identity explosion, NHI-related data breaches, NHI terminology, taxonomy of AI agents, RAG, autonomous AI agents, and AI workflows
20 NHI and AI agent risk vectors you need to know
We’ll dive deep into the top 20 risk vectors affecting non-human identities and AI agents, spanning everything from orphaned credentials and secrets sprawl to prompt injection and insecure plugin integrations. You’ll learn how attackers exploit insecure defaults, over-scoped permissions, lateral movement, and weak isolation across services.
You’ll understand the major security risks, supported with examples from attacks, OWASP reports, and vulnerabilities discovered by security researchers.
Topics covered: Over-scoped permissions, orphaned NHIs, NHI authentication, secrets, 3rd party vulnerabilities, token reuse, lateral movement, multi-tenant data leaks

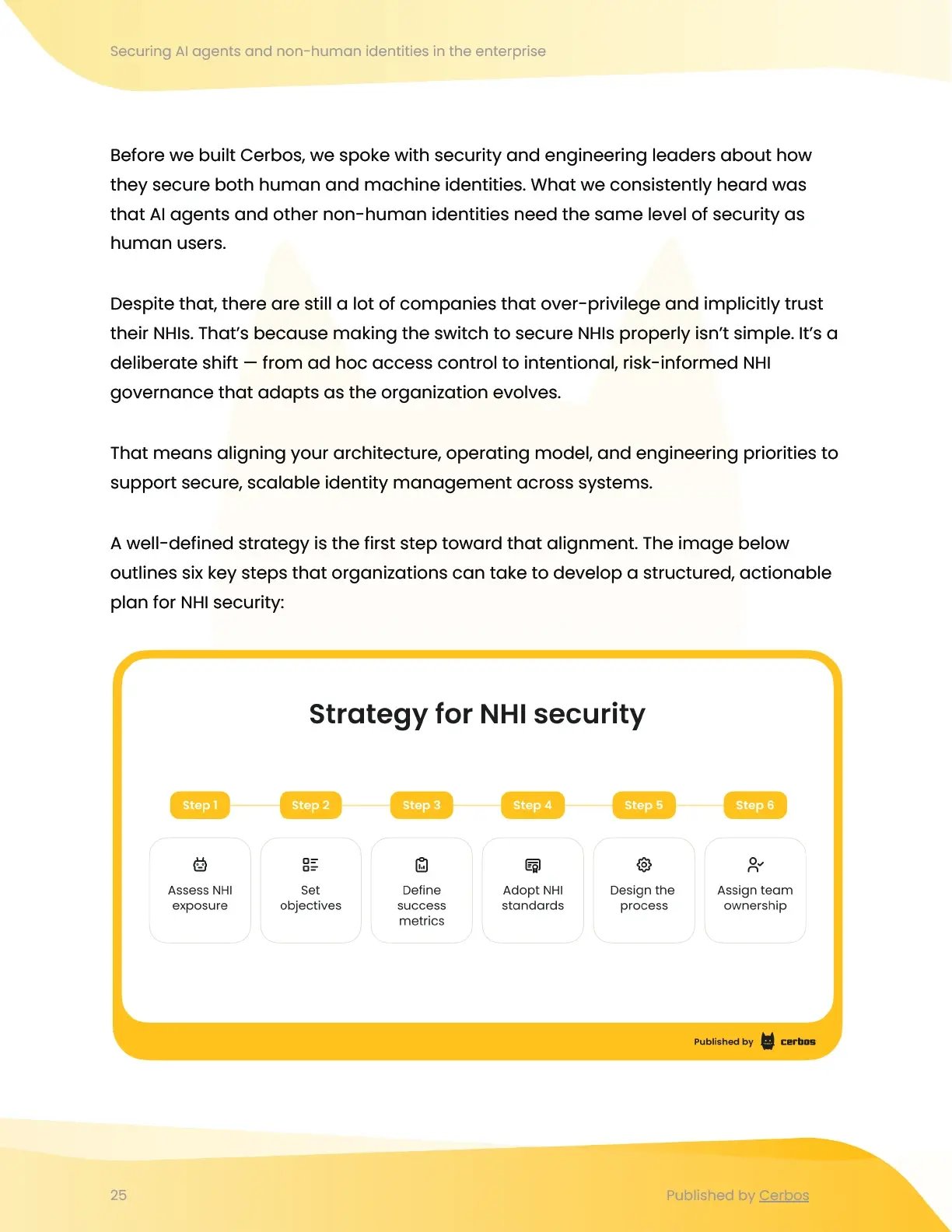
Strategies and principles for NHI governance
We’ll cover practical strategies for securing NHIs, starting with exposure assessment, setting measurable objectives, and aligning Zero Trust controls across architecture and teams. These are backed by 12 security principles and 35 implementation steps to drive NHI governance.
This section will provide you with the NHIs' security checklist, covering inventory management, credential isolation, least privilege, fine-grained access control, and externalized authorization, mapped to practical implementation steps.
Topics covered: Zero Trust Security, SPIFFE, WIMSE (IETF), SPICE (IETF), OpenID Connect M2M, FIDO Device Onboarding (FDO), NIST SP 800-207 Zero Trust Architecture
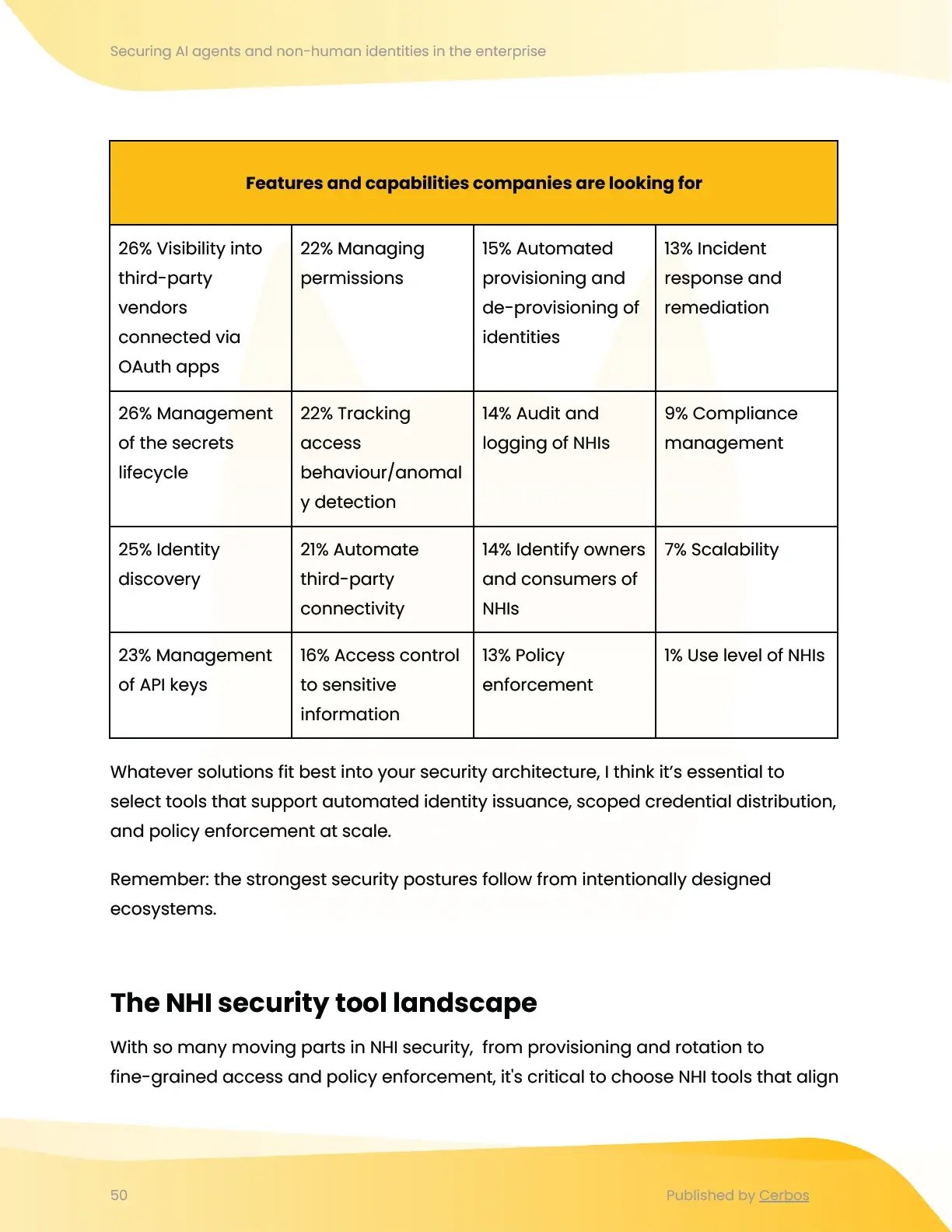
Vendor landscape and vendor evaluation checklist
Securing NHIs means aligning security controls across the entire identity lifecycle—from issuance to revocation. In this chapter, we break down how to evaluate vendors based on your architecture, maturity, and specific use cases. Rather than aiming for tool breadth, we show why depth, interoperability, and lifecycle fit matter most.
You’ll learn how to assess solutions for provisioning, rotation, access control, and policy enforcement in a way that supports scalable, Zero Trust NHI security.
Topics covered: NHI security architecture, automated identity issuance, scoped credential distribution, policy enforcement at scale, NHI security tool landscape
Bonus: A comprehensive list of NHI security vendors
We’ve compiled a thorough list of NHI security vendors that can help you close this security gap before attackers make use of it.

About the author
Emre Baran, co-founder of Cerbos, ex-Googler, entrepreneur & software executive with 20+ years of experience.
Some insights from NHI experts
featured in the ebook

Attackers don’t break in — they log in, and non-human identities are one of the easiest attack vectors. Because AI agents and service accounts can’t enroll in MFA, often have high privileges, and their credentials are rarely rotated, adversaries use them to move laterally with little friction.
Without deep visibility and detection capabilities for NHIs, a single compromised key can turn into a significant breach.
Vincenzo Iozzo
CEO at SlashID
The hardest part for any organization is having an inventory of what’s interconnected across your environment.
You need to know which keys and tokens are active, which are stale, and what technologies they’re connected to.
Kyle Kurdziolek
VP of Security at BigID
There’s a real Eureka moment when organizations realize how many non-human identities exist under the surface and how little visibility they had until now.
It’s even more striking when they uncover how many of those identities and their secrets have excessive access by default.
Nirit Icekson
CMO at Entro Security
Security teams often put guardrails around NHIs but forget to tell the story behind them. What happens when you authorize an agent? Sync your calendar to a random tool?
Most people don’t realize they’re giving that identity access to Zoom meetings, agendas, and sensitive event details. If users understood the threat and the risk, they’d think twice. Security’s job is to help people see the risk of the action they’re about to take.
Branden Wagner
Head of Information Security
Secure non-human
identities at scale
Manage permissions for workloads, microservices, AI agents, and API clients with flexible, policy-driven authorization.