Fixed roles break under enterprise scale
When a 30,000-person organization signs up for a SaaS product, the "Admin, Editor, Viewer" model becomes a cage. Role explosion, endless support tickets, and blocked productivity follow. One size does not fit all.
Every enterprise customer has unique organizational structures, complex hierarchies, and distributed teams. The "North America Marketing Content Editor" needs different access than the "EMEA Financial Reviewer." Matrix reporting, regional compliance requirements, and specialized functions demand granular, contextual permissions that static roles simply can't provide.
This ebook reveals how leading SaaS companies implement dynamic multitenant authorization that scales from 10 users to 30,000 - without role explosion.
![[eBook] One size does not fit all: A guide to multitenant authorization [eBook] One size does not fit all: A guide to multitenant authorization](https://solutions.cerbos.dev/hs-fs/hubfs/multitenancy_Ebook_Cover%20(4).png?width=1550&height=2000&name=multitenancy_Ebook_Cover%20(4).png)


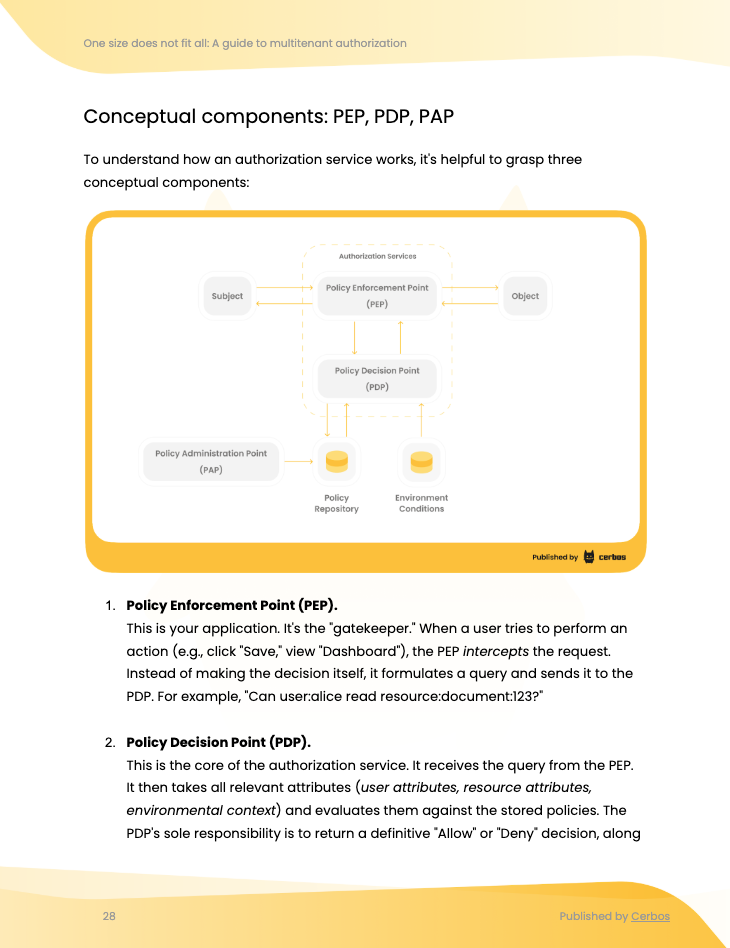
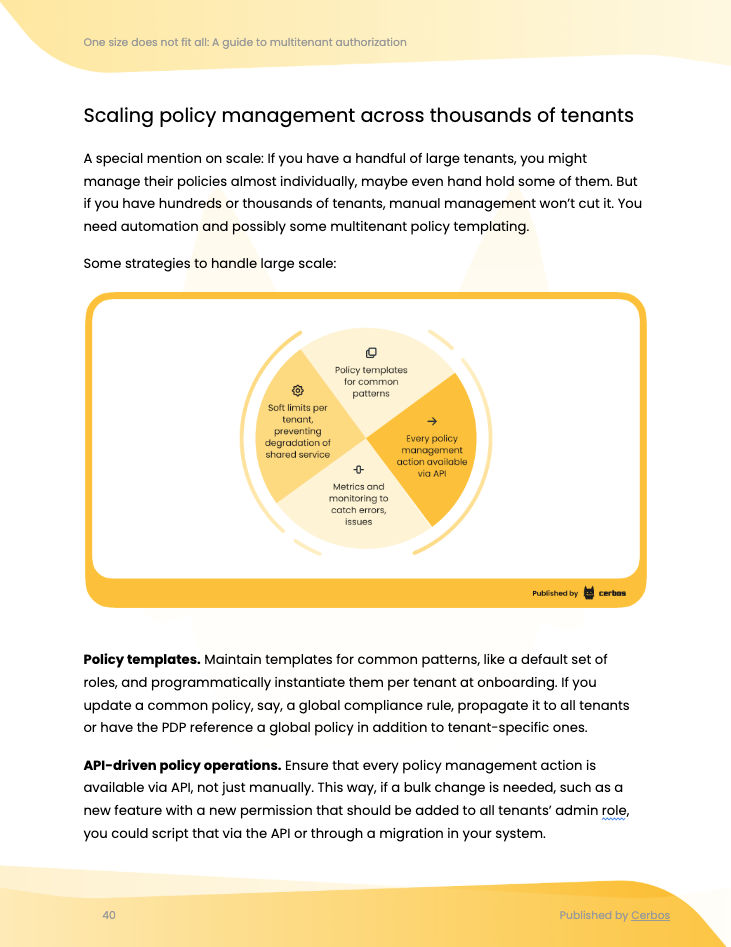




.png?width=2000&height=1125&name=externalized%20authorization%20ebook%20webinar%20page%20image%20(8).png)
.png?width=2000&height=1125&name=mcp%20ebook%20pop-up%20image%20(3).png)